What Is Conditional Access & What It Means For Your Business
Want an insider scoop on what we think will be the next big thing in the world of security? Conditional access will be the security policy all companies need to put into place if they want their security up to date. This policy focuses on protecting the user instead of just the device. But why is that? The end-user has become more of a security risk than ever before, with the added risk of remote working now thrown into play, it’s crucial to have a focus on not just the devices, but the actual end-user! The end-user has become more of a security risk than ever before, and with the added risk of remote working now thrown into play, it’s crucial to focus just as much on actual end-users as well as your overall business.

What Is Conditional Access?
Conditional access is the extra layer of protection which protects the end user instead of the actual device. It brings signals together, to make decisions and enforce organisational policies. Essentially, conditional access is based on certain predetermined conditions or criteria, such as the user’s identity, the device they are using, the location they are accessing the system from, and any other security factors your business may have. The goal of conditional access is to ensure that only authorised users are able to access sensitive information, and that access is granted only under specific, secure conditions.
The key to getting into any device is the end user. As long as the end user knows their username and password, they’re at risk. Once both of those are protected, it becomes incredibly difficult for hackers to access devices. With hacker activity increasing every day it is crucial now more than ever to level up your organisation’s security! No matter how big or small, Cyber Security has become essential for all.
Protecting The User
Protecting the user instead of the device gives employees the ability to “work from anywhere”. Even though businesses are trying to get away from remote working and bring back working in the office, employees have become accustomed to it, which means companies are now inclined to add extra protection. Employees are able to work from anywhere, which in turn can leave your business and its systems open to threats. If an employee is travelling to a meeting and needs to check in on some customer data along the way, conditional access ensures whatever device they are using has the correct levels of security in place.
Without conditional access implemented in this scenario, the employee and the data they hold will be at risk of getting exposed. Now imagine a company owner knew this, they would ensure employees could only access data while on company premises right?
What have we been told are the basics of security within businesses?
Secure your devices right?
Well, it’s more than that. The end user’s identity is just as important as the devices. Modern-day security now extends beyond an organisation’s network, it now includes a user and device identity. You can secure everything, all devices such as laptops, desktops, phones and tablets. When each employee has more than one device, they have an even higher chance of exposing company data, which can dramatically increase your organisation’s overall risk of cyber attacks and breaches. Let’s say you were an employee in a big organisation, and they have provided you with a laptop and a phone, those devices aren’t secure until they have conditional access policies implemented.
Securing Your In-House Devices Isn't Enough Anymore!
Many companies have secured their in-house desktops, however with the onset of the pandemic, some company devices have left office spaces without adequate security measures in place. This has made these devices more prone than ever to attacks without the end user even realising them. As a result of these unsecured devices, it’s extremely risky for employees to be able to work in different areas.
However, organisations can now use conditional access policies as part of their access control decisions. This allows the organisation to determine what level of access the end user is allowed while working from anywhere. With the change in computing to a more cloud-centric model, it has proven to be more difficult to control access, to the documents and data that an organisation depends on to run a business. The conditional access policy lets you ensure only devices enrolled on Mobile Device Management can access office 365.
How Conditional Access Systems Work With Unsecure Devices
With conditional access implemented in your business, you’ll have that extra layer of protection around the end user wherever they decide to work.
So how does conditional access work specifically?
For your employees to be able to log into a device securely, the device will have to go through a virtual checklist. This will ensure that all the work your employee is doing on their device is secured at all times, greatly limiting the overall risk posed by working outside the office.
Let’s add an analogy to explain this better, devices normally have a firewall implemented into the system right? Well, with conditional access implemented, the user has a constant firewall around them. Meaning whatever device they access, has to be up to the standard and policies the company has put into place.
There are two primary goals with conditional access
- Empower users to be productive wherever and whenever
- Protect the organisation’s assets
Companies use conditional access policies to apply the right access controls when needed to keep their organisation secure – As seen in the image below conditional access secures a device through signals, such as the user’s location, which then has to go through a verification process in order to access company data and applications.
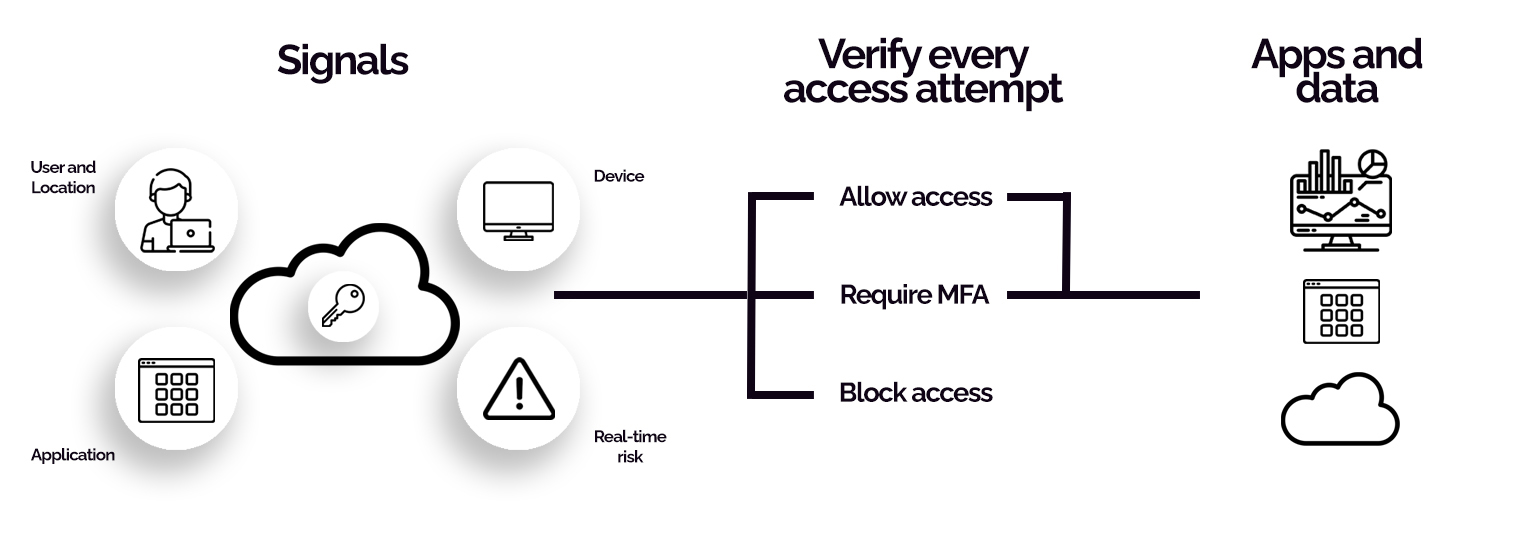
The policy put into place is completely up to what the business’s standards of security are. However, they all decide whether they want to implement MFA (Multi-Factor Authentication) in their access attempt. To put conditional access policies in their simplest form, they’re known as “if-then” statements. Essentially “if” a user wants to access a resource, “then” they must complete an action. Let’s say a payroll manager wants to access the payroll application and is required to do MFA to access it. That would be an example of a conditional access policy.
Common Signals?
We’ve mentioned the different types of policies businesses put into place, but what does that mean? It means the company decides what level of security they wish to make the user go through. This will be determined by the user’s job role and responsibilities.
Think of a signal as an added security measure to make sure the policy is taking place under the right circumstances. Conditional access relies on signals to inform the system about the state and trustworthiness of the device. This happens prior to the device gaining access to the data. These policies bring signals together to make decisions and enforce the policies.
Let’s add an example to better explain this. If there’s a policy where a device will need the newest update of outlook, the signal implemented will ensure that the update is there, if not the user and device won’t have access to what they choose.
Here are some common signals which are implemented into conditional access:
User or a group membership
Policies can be targeted to specific users and groups giving administrators control over access
IP Location Information
Organisations can name locations defined by IP address ranges to be trusted named locations. Sign-ins from trusted named locations improve the accuracy of Azure AD Identity Protection’s risk calculation, lowering a user’s sign-in risk when they authenticate from a location marked as trusted
Device
Users with devices of a specific state can be used when enforcing conditional access policies.
Real-Time and calculated risk detection
Signals integration with Azure allows conditional access policies to identify risky sign-in behaviour. The policies can then force users to change their passwords and to do MFA to reduce their risk level.
Microsoft Defender for Cloud Apps
Enables user application access and sessions to be monitored and controlled in real-time, which will ultimately increase visibility and control over access to the cloud environment.
Application
Users attempting to access specific applications can trigger different conditional access policies.
What Does This Mean For Your Company?
The world is becoming more vulnerable to cyber-attacks every day. As a result, having the right level of cyber security is essential for all organisations. With conditional access policies implemented in your business, your company’s cyber attack risk is reduced significantly.
Many companies have and are currently moving their infrastructures online through systems such as company portals. Conditional access is there to safeguard this system since these portals hold large amounts of personal and sensitive data. The online identities of employees have become the main access point for hackers. Managing and securing these identities can help prevent cyber infiltration. For a hacker, a user can be a “key” to get into any business and access their data. Once the identity of the user is exposed, the whole company is vulnerable.
Conditional access doesn’t just stop potential hackers from gaining access to your data. The policies go the extra mile and ensure any employee which has left the business, can’t access any of the data through devices such as laptops, phones or even tablets. However, why is this so important? It ensures that your company data is secure no matter the circumstance, giving you the ability to block access to anyone, including employees.
Let's Get Technical
The idea of conditional access is based all on the end user’s username and password. Conditional access allows the user to have a firewall around themselves instead of just the device. Therefore, whenever the user wants to work somewhere other than their office, they can do so with the peace of mind that they are protected. It makes sure the device they are occupying is up to the security standard the company has put into place.
Essentially, companies implement conditional access policies. These policies may include things such as MFA (multi-factor authentication) or blocking risky sign-in behaviours. Essentially what it means is it verifies whether you are allowed access to login to this specific device.
Convinced Yet?
In fewer words, conditional access is an extra layer of security to help protect the user’s identity and business assets when devices, such as laptops are taken out of secure office spaces and used remotely. As we move into an age where remote working is becoming more and more common, conditional access is essential for businesses. That’s why we think this security policy is the next big thing because it will have people thinking about security in a whole different way. As much as securing a device is important, ensuring a user has an active, constant firewall around them is just as important to protect themselves and your business.
